phpMyAdminに深刻な脆弱性があるため、ハッカーがデータベースを損傷できる
管理者をだましてリンクをクリックさせるだけである。ハッカーはデータベースに有害なリモート操作を実行する。これはphpMyAdminの深刻なセキュリティホールです-MySQLデータベース管理アプリケーション。
2020年07月01日

管理者をだましてリンクをクリックさせるだけである。ハッカーはデータベースに有害なリモート操作を実行する。これはphpMyAdminの深刻なセキュリティホールです-MySQLデータベース管理アプリケーション。
管理者をだましてリンクをクリックさせるだけである。ハッカーはデータベースに有害なリモート操作を実行する。これはphpMyAdminの深刻なセキュリティホールです-MySQLデータベース管理アプリケーション。

インドのセキュリティ研究者であるAshutosh Barotによって発見されたCSRFの脆弱性は、phpMyAdminバージョン4.7.x(4.7.7より前)に影響を与える。
CSRFの脆弱性を利用するために、ハッカーはユーザーをだまして特別なURLをクリックさせる。これにより、レコードの削除、テーブルの削除/切り捨てなど、データベースに有害な操作を実行できる...
phpMyAdminは、MySQLおよびMariaDB用の無料のオープンソース管理ツールであり、WordPress、Joomla、およびその他の多くのコンテンツ管理プラットフォーム上のWebサイトのデータベース管理で広く使用されている。

さらに、多くのホスティングプロバイダーは、顧客がデータベースを便利に整理するためにphpMyAdminを使用している。
研究者はまた、リモートで特別なリンクをクリックするように仕向けることで、ハッカーがデータベース管理者にデータベースからテーブル全体を誤って削除(DROP)させる可能性があることを示すビデオも公開した。
バロットは、GETクエリを使用し、DROP TABLE table_nameのようなデータベース操作のためにPOSTクエリを使用するphpMyAdminの機能について説明した。GETクエリはCSRF攻撃から保護する必要がある。この場合、POSTクエリが使用され、URL経由で送信されました(おそらくマーキングの目的で)。これにより、ハッカーはデータベース管理者をだまし、ハッカーの選択でテーブルのドロップデータベースクエリをクリックして実行することができる。ただし、この攻撃は簡単に検出されるため、実装は簡単ではない。CSRF攻撃URLを準備するには、ハッカーはデータベースとターゲットテーブルの名前を知っている必要がない。
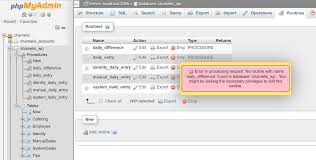
ユーザーが挿入ボタンをクリックしてデータベースでクエリを実行すると、DROP ... URLにはデータベース名とテーブル名が含まれる。この脆弱性は、URLがブラウザー履歴、SIEMログ、ファイアウォールログ、ISPログなどのさまざまな場所に保存されるため、機密情報が漏洩するリスクにつながる可能性がある。
研究者はこの脆弱性をphpMyAdmin開発者に報告し、確認された。また、この脆弱性を処理するためにphpMyAdmin 4.7.7をリリースしました。 したがって、管理者はすぐに更新することをお勧めする。
ベトナムでアウトソーシングを展開するオフショアパートナーをお探しの場合は、ベトナムに長年在籍している企業以外にも、ハチネットは以下の特徴を体験できる場所です。
Microsoft .NET Webサイト開発(asp、vb.net ...)
ウェブサイト開発フォント終了
Javaシステム/アプリケーション開発
モバイルアプリケーション開発(IOS / Android)。
Cobolシステム開発。
私たちにもサービスがあります
柔軟なオフショア開発
BrSE担当者を日本に派遣
現在、Hachinetのパートナーの80%は日本のソフトウェア企業であり、当社のエンジニアは、高い技術を持つだけでなく、お客様と日本語で直接にコミュニケーションをとることができる。
Hachinetは、常にソフトウェアの品質と顧客の満足度を重視している。当社のITアウトソーシングサービスを選択すれば、製品が実装されてから納品されるまで安心できると信じる。
メールでご連絡ください:contact@hachinet.com
- オフショア開発
- エンジニア人材派遣
- ラボ開発
- ソフトウェアテスト
電話番号: (+84)2462 900 388
メール: contact@hachinet.com
お電話でのご相談/お申し込み等、お気軽にご連絡くださいませ。
無料見積もりはこちらから